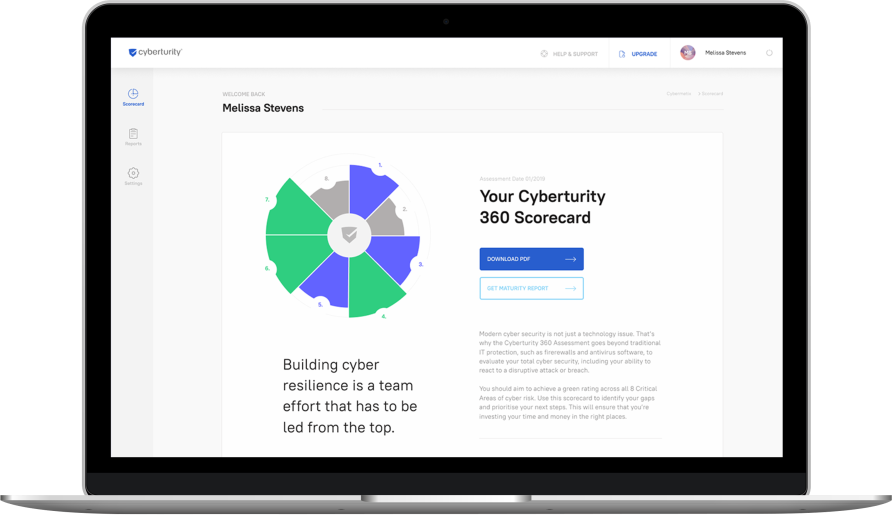
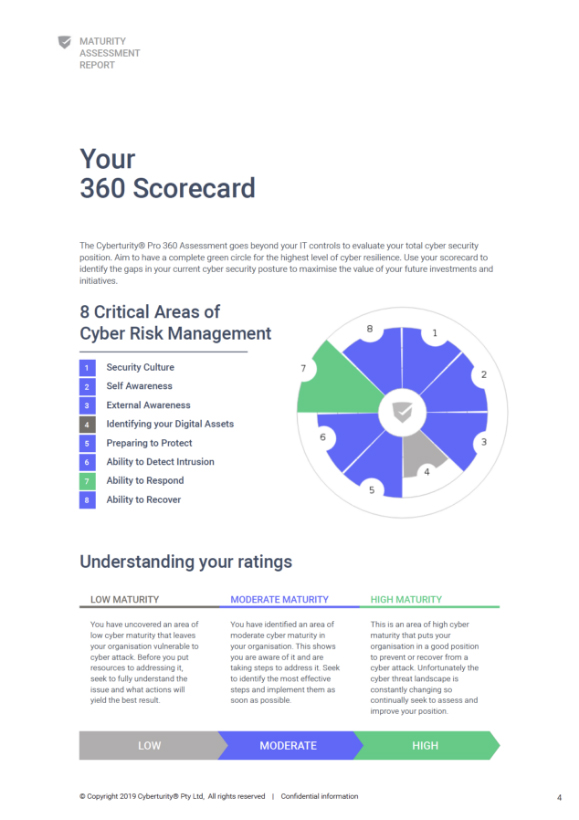
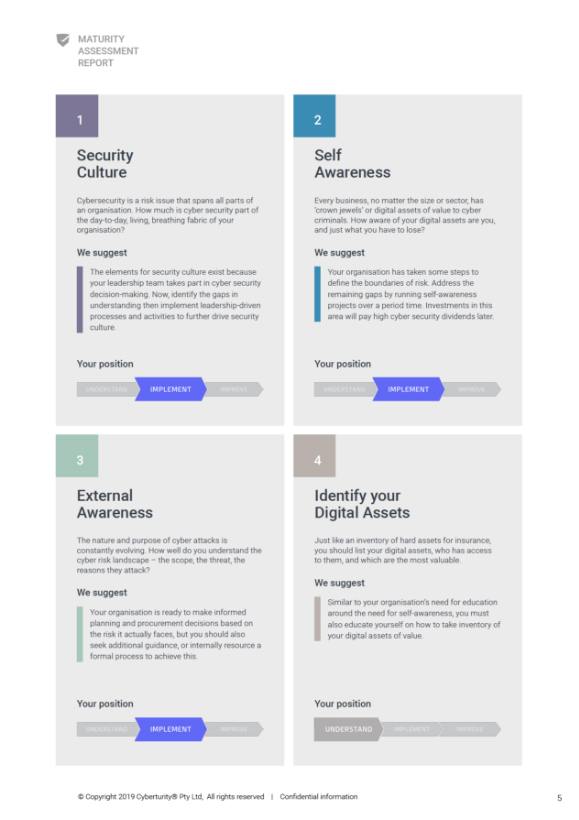
We’ve specifically architected a platform that is designed to keep personal information and maturity assessment data secure. We utilise industry-best practices, such as multi-factor authentication and data isolation, and can ensure that we treat all sensitive information as we would our own.
The use of multi-factor authentication strenghts credentialed access to build a significant and robust barricade between any malicious actors and your personal information. Our onboarding process is simplified through the use of the “best of breed” credentialing system which allows for secure, streamlined provisioning and ongoing management of our users.
All personally identifiable information and corporate information that we collect during the provisioning process is kept completely isolated from all response data we receive during our assessment evaluations.
This assessment data is further isolated from the public internet, providing an additional level of security. Even in the highly unlikely event that this data was to be somehow breached, it is rendered wholly unusable, as we relate your answers to a tokenised version of the credentialed user. Isolation is a key process we employ in our provisioning and maturity assessment user interface, which keeps the two stages completely separate from each other.
We pride ourselves on our implementation of the leading edge techniques and technologies provided by the world’s top trusted platform providers. Our goal is to quickly and painlessly provision our clients into a secure platform that keeps the maturity assessment data they provide and the assessment reports safe, private and in the hands of the only people who should see it: You.